- Home
- About Us
- The Team / Contact Us
- Books and Resources
- Privacy Policy
- Nonprofit Employer of Choice Award

 Nightmare headline—“900 SINs stolen due to Heartbleed bug: Canada Revenue Agency.” Just substitute “credit card numbers” and the name of your charity to complete the worst-case scenario for an Executive Director. If your charity has a web site but not an IT department to protect it, what do you do?
Nightmare headline—“900 SINs stolen due to Heartbleed bug: Canada Revenue Agency.” Just substitute “credit card numbers” and the name of your charity to complete the worst-case scenario for an Executive Director. If your charity has a web site but not an IT department to protect it, what do you do?
To understand your charity’s exposure, let’s start with the current issue. What is this Heartbleed bug that has caused all this destruction? Without getting too technical, it is hacking software that takes advantage of a vulnerability in a common utility used to establish a secure connection between two computers across the internet. What makes this so scary for charities is that there was no cloak and dagger here, no malicious plot directed at one organization—anyone could be targeted. In fact, hackers can just sweep the internet randomly, looking for vulnerable web sites. 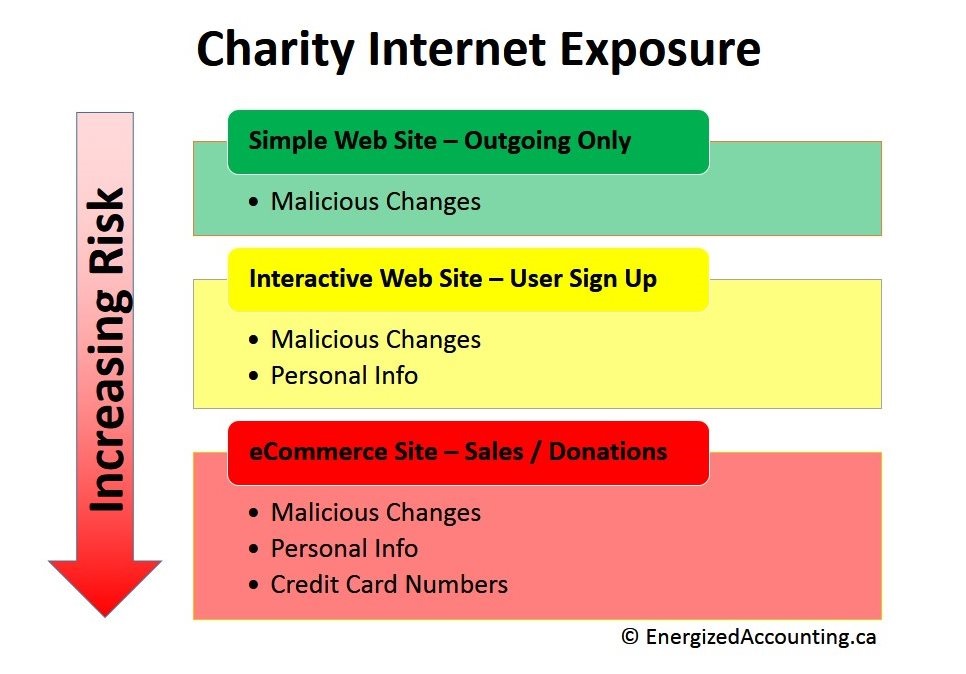
How do you protect yourself? Start by assessing the risks you face while planning your strategies. The above chart divides charity web sites into three categories of increasing risk. Often, a charity’s first web site is volunteer driven, based on current fundraising documentation. As the organization looks to increase donor engagement, the web site may become more interactive to include user feedback, sign-up forms and discussion forums. Finally, the website may evolve into part of the fundraising strategy, accepting donations and making sales.
Risk protection strategies
Here is an overview of some of the risks and strategies charities should consider when determining their internet presence.
Simple web sites
Risks
Interactive and eCommerce websites
RisksOf course, there are general risk mitigation strategies that you should always employ. These would include recruiting technical professionals to your Board, putting the organization’s policies in writing and keeping your insurance agent and coverage up-to-date with your activities.
Finally, recognize that you can have the most secure web site and still be attacked. For example, a national charity received hundreds of $5 donations through their web site. A few days later, rejection notices from credit card companies started pouring in. Upon investigation, it was determined that someone was putting through the donations to test which (stolen) credit card numbers were still valid. To make matters worse, the credit card processing company charged a fee for each rejected credit card. To address the problem, they made arrangements with the credit card company not to process small, repetitive transactions until they were investigated. They also took their online donations page offline for a week so that the perpetrators would move on.
All in all, it is best to review your website through a risk management lens. Depending on the type of website that you have, there are strategies to choose from that will suit your needs—and protect you from security vulnerabilities like the Heartbleed bug.
Bill Kennedy is a Toronto based Chartered Accountant with Energized Accounting, focusing on financial and reporting systems in the charitable sector. He blogs at www.EnergizedAccounting.ca/blog/. Find out more at www.EnergizedAccounting.ca; follow Bill @Energized